Blogs
Your HPE-Juniper networking install base… and why it’s basically your linen cupboard at home
How is your network install base like your linen cupboard? Stay with me.
Read More

Mist IoT Assurance provides a simple yet comprehensive way to onboard client devices without relying on a client MAC address, allowing dynamic traffic engineering and enforcing granular network access control. The service reduces overall IT operational cost with Pre-Shared Key (PSK) life cycle management and organisation-level visibility at cloud scale.
Mist™ Access Assurance is a microservices-based, cloud network access control (NAC) service that enables enterprises to easily enforce a Zero-Trust security model.
Access Assurance solves many complexity challenges associated with traditional NAC offerings by:
Access Assurance extends beyond the capabilities of Juniper Mist IoT Assurance, which simplifies onboarding for headless IoT and BYOD devices. With Access Assurance, IT teams can onboard wired and wireless devices with 802.1X authentication or MAC Authentication Bypass (MAB) methods, even for non-802.1X devices.
IoT Assurance provides a simple yet comprehensive way to onboard client devices without relying on a client MAC address, allowing dynamic traffic engineering and enforcing granular network access control. The service reduces overall IT operational cost with Pre-Shared Key (PSK) life cycle management and organisation-level visibility at cloud scale.
Juniper Mist IoT Assurance is a “MAC-less” and “NAC-less” onboarding service that can leverage MPSK as a device type and user/endpoint identity/.
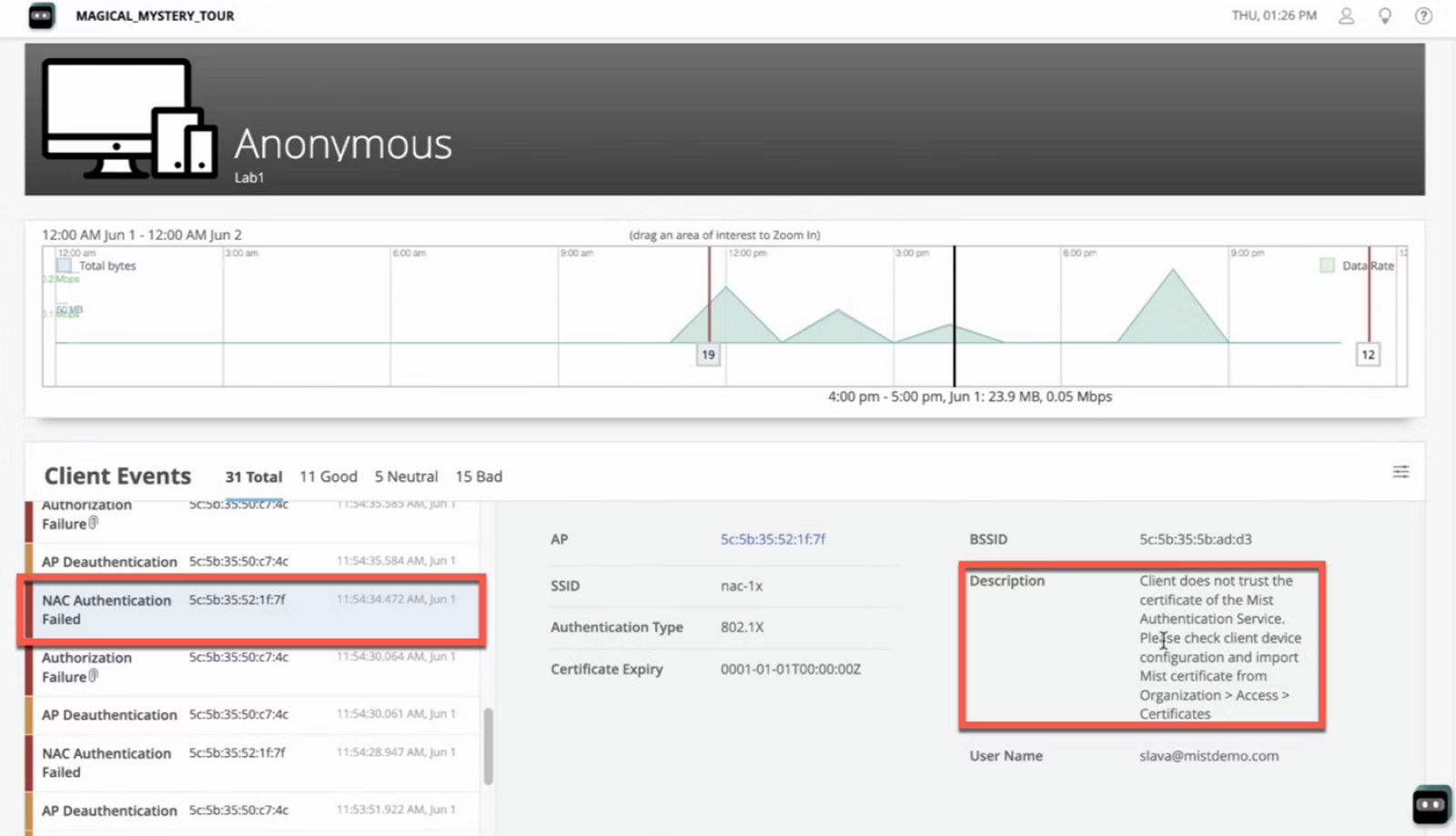
Access Assurance provides end-to-end connectivity troubleshooting in a unified view from the client, network infrastructure, and access control perspective, dramatically simplifying Day 2 support.
IT admins gain a cohesive view of the end user experience and can determine whether poor experiences are due to client configuration, network infrastructure, authentication, or a service.
Juniper Mist cloud helps simplify day-to-day operations by easily identifying if an end user connectivity issue is caused by a client configuration mistake, network infrastructure and service problems or authentication policy configuration issues. The Juniper Mist service level expectations (SLEs) for wired and wireless clients are enhanced to include network access events, such as authentication events, certificate validations, and more.
Based on user and device identity, Access Assurance can instruct the network to assign a user to a specific network segment (VLAN or a group-based policy tag), as well as enforce network policy by assigning a user role. Such roles can be leveraged in the Juniper Mist WxLAN policy framework or switch policies.

New features, security patches, and updates are automatically added to Access Assurance on a bi-weekly basis without interruptions or service downtime. This capability dramatically simplifies and improves service operations for network IT administrators, eliminating lengthy software upgrades and service downtime.
On-Demand Resources: The SaaS model allows for automatic scaling of resources to accommodate increasing numbers of users, devices, and data. This means you can easily handle spikes in network activity without manual intervention.
Cost Efficiency: Pay-as-you-go pricing models enable organisations to scale up or down based on current needs, avoiding the need for significant upfront investments in hardware and software. Juniper Mist Access Assurance offers centralised management through the Mist cloud-based portal, simplifying the administration of network policies, user access, and device management across multiple sites and geographies.
Blogs
How is your network install base like your linen cupboard? Stay with me.
Read More
Blogs
A recent ED trip with one of the kids revealed a surprisingly accurate triage wait-time counter. I expected a feel-good dummy number — but nope, it actually worked.
Read More
Technical
Whether you're just stepping into the world of monitoring or you've been staring at Zabbix dashboards for years, it helps to understand how all the pieces fit together. Zabbix relies on a few key components—like servers, agents, and proxies—to keep an eye on your environment. Here's a quick...
Read More